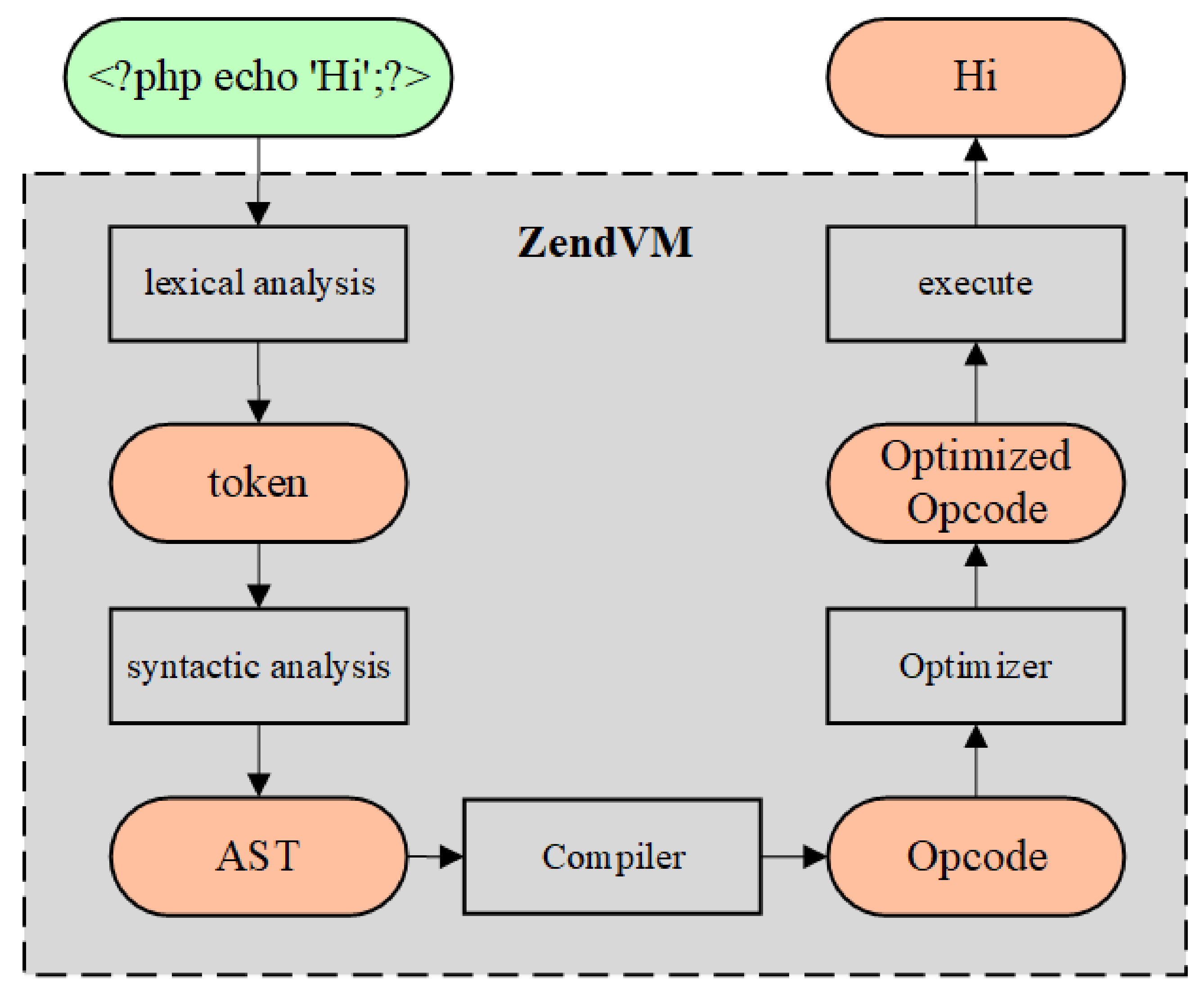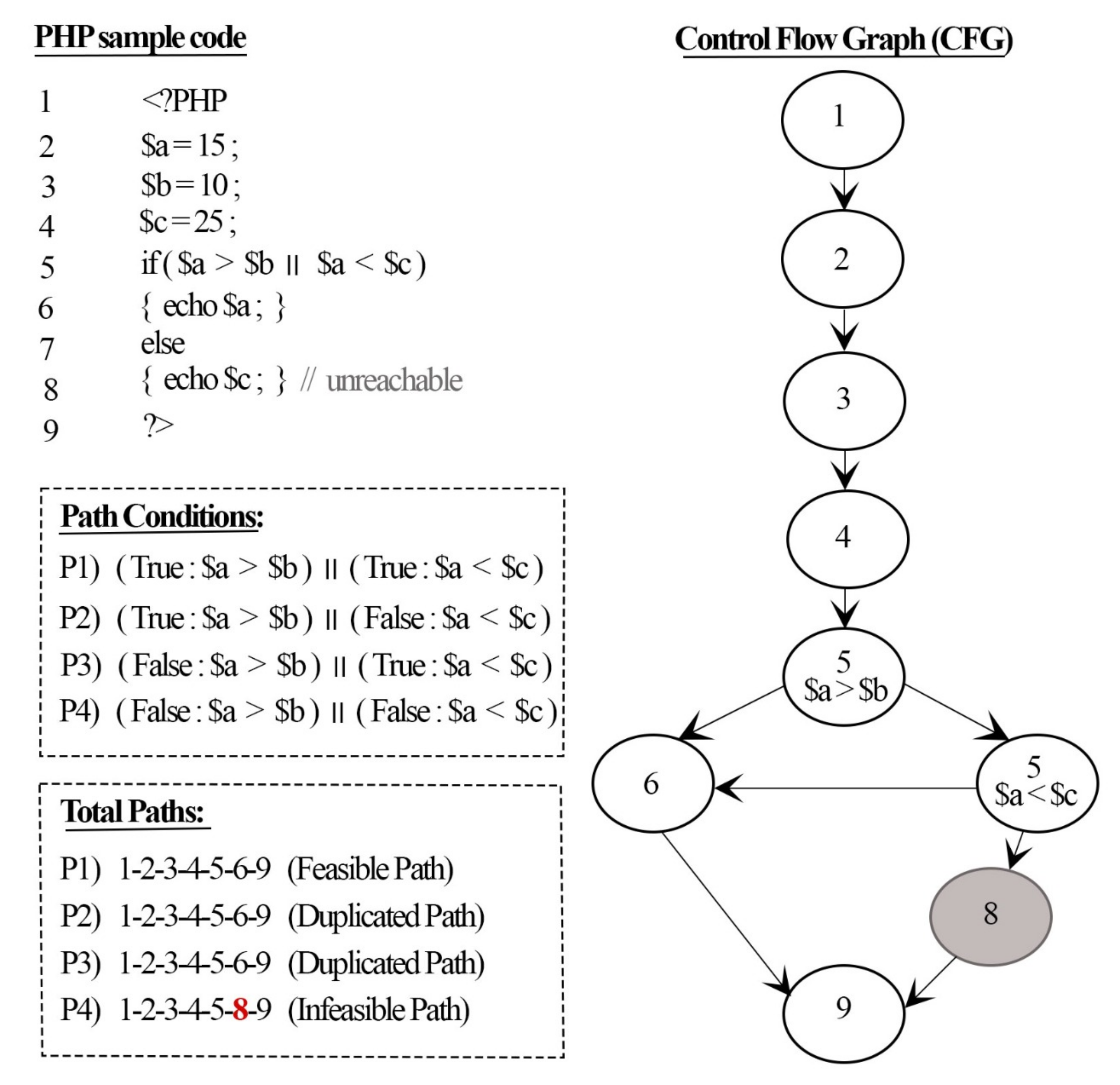
Applied Sciences | Free Full-Text | An Approach for Detecting Feasible Paths Based on Minimal SSA Representation and Symbolic Execution
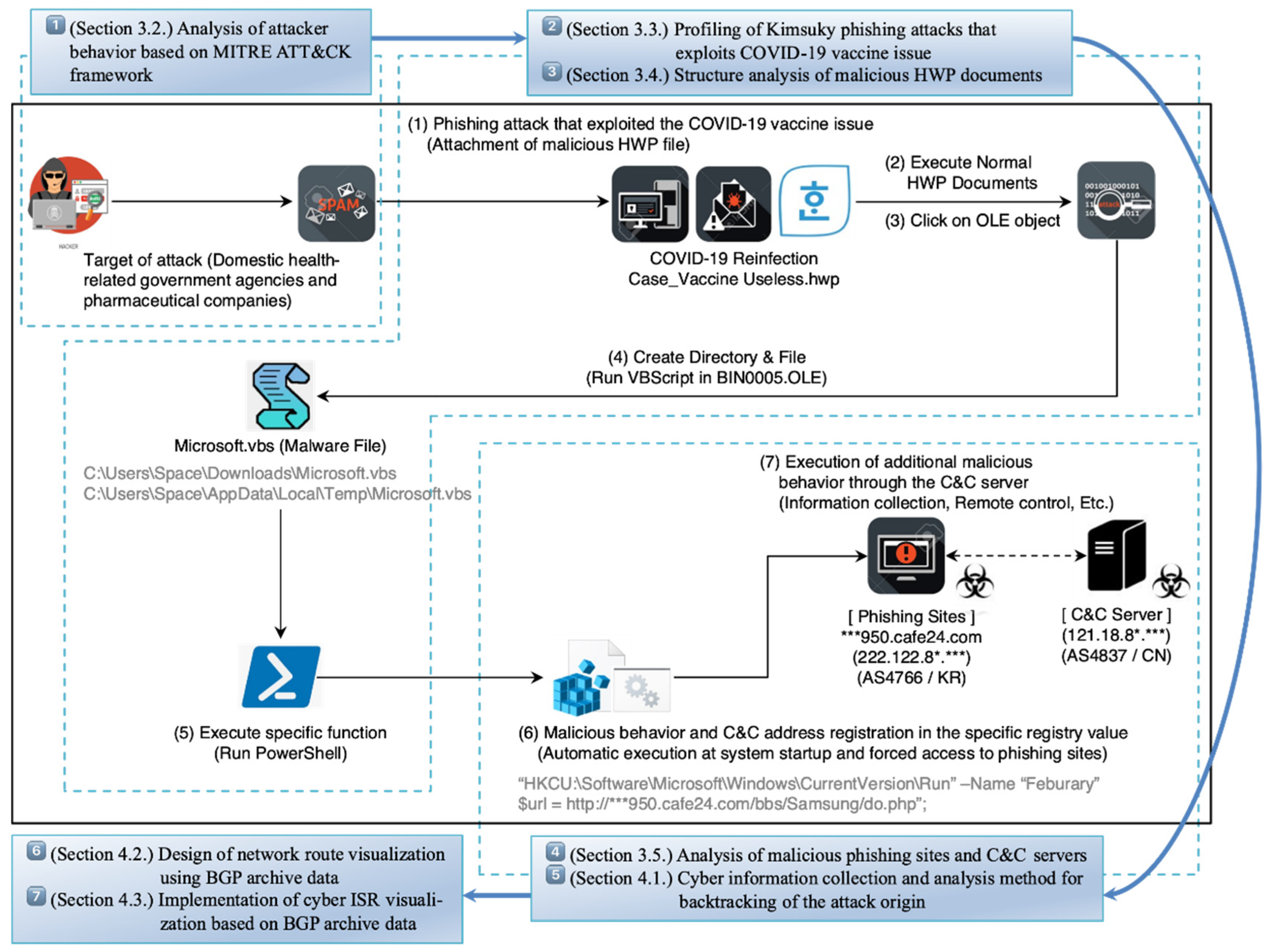
Electronics | Free Full-Text | Research on Cyber ISR Visualization Method Based on BGP Archive Data through Hacking Case Analysis of North Korean Cyber-Attack Groups


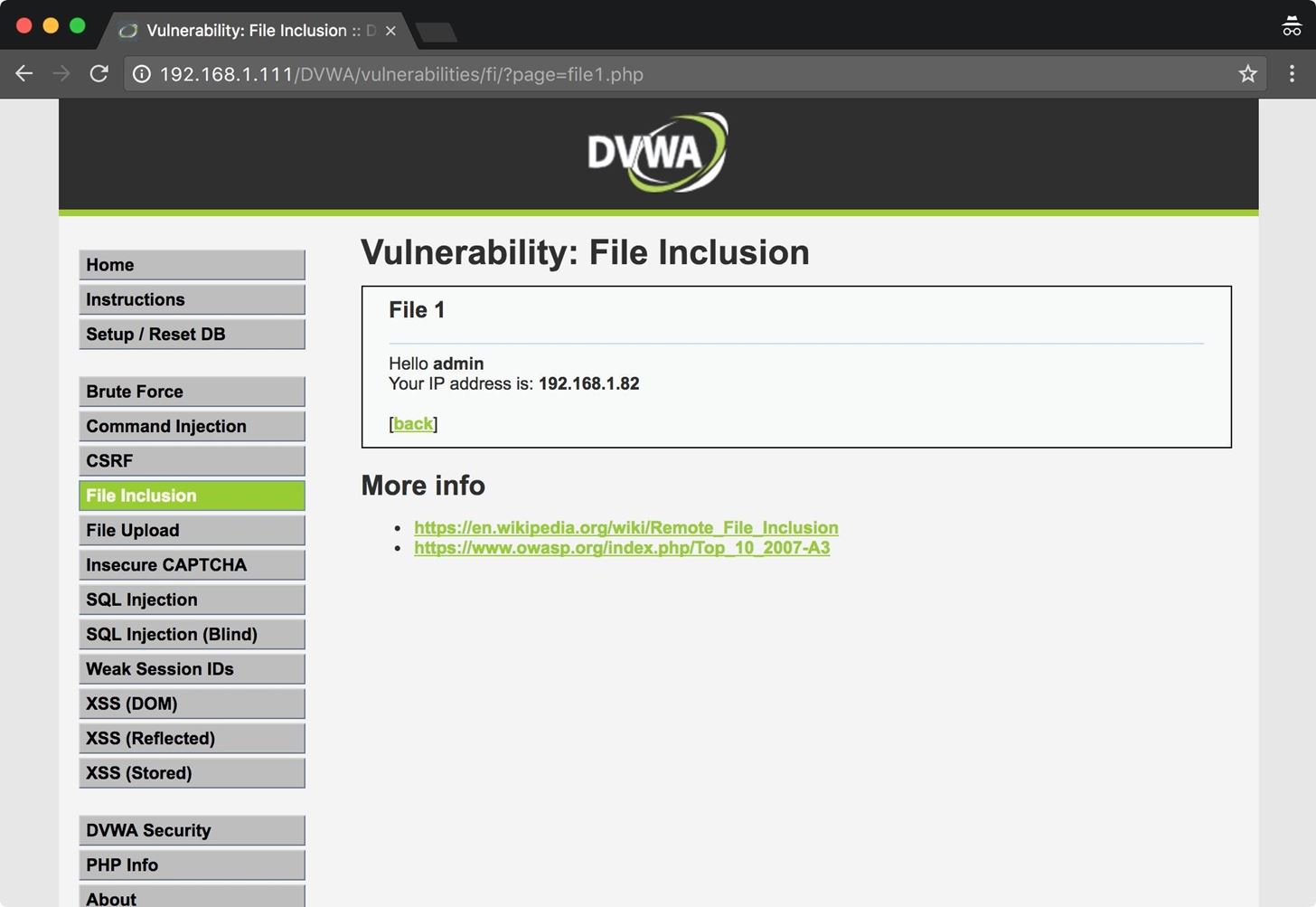
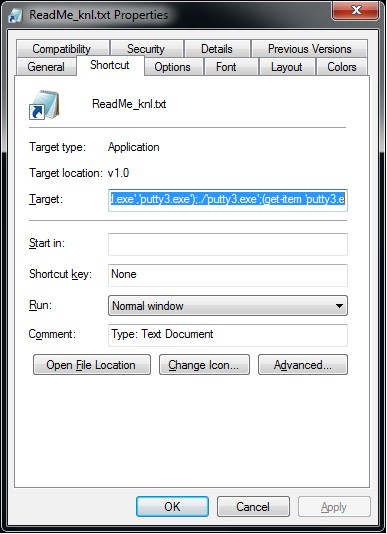

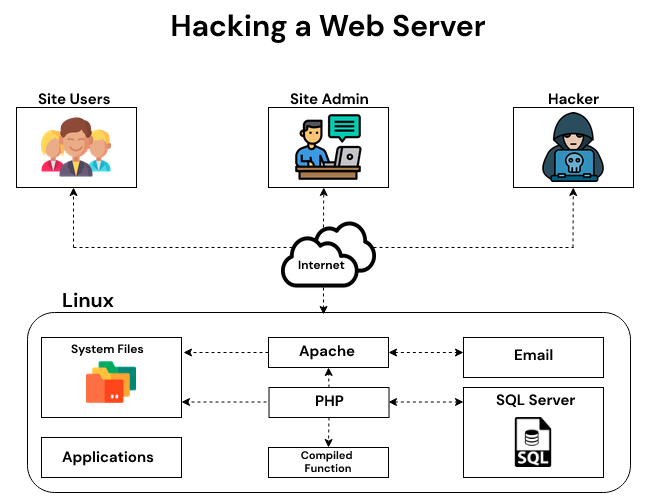

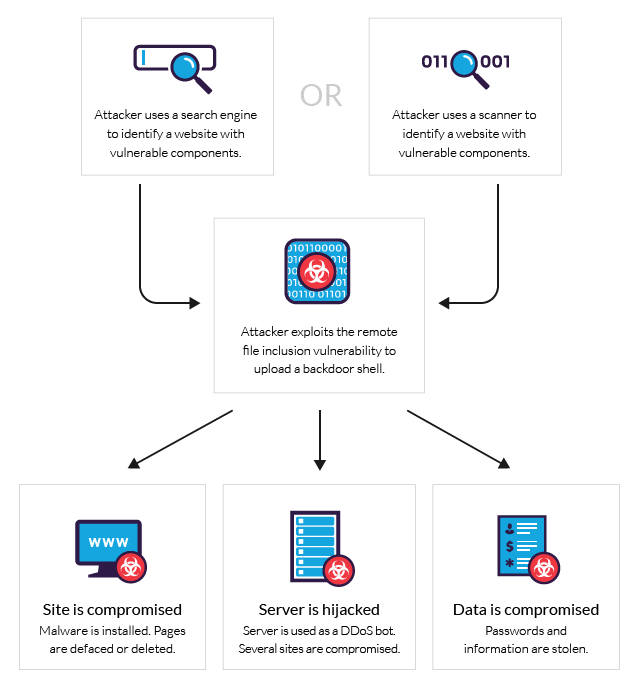
![How To Hack Any Website. [PART -3 Exploiting Trust] | by Niveet Palan | System Weakness How To Hack Any Website. [PART -3 Exploiting Trust] | by Niveet Palan | System Weakness](https://miro.medium.com/v2/resize:fit:750/1*EiOdBhpzaEQXST7AZhtzJA.png)